Tryhackme - Windows Forensics 1

Category: CTF
Posted at: Jul 8, 2025
4 Minutes Read
The field of forensics caught my attention, not only is it interesting, but it's also very useful. This marks the beginning of my learning journey in digital forensics. TryHackMe offers several rooms dedicated to learning forensics, and this is one of them.
This room focuses on Windows forensics, as the name suggests. It mainly involves extracting information from different registry hives. A Registry Hive is a group of Keys, subkeys, and values stored in a single file on the disk (tryhackme).
In this blog, I’ll be solving the challenge in the room and explaining my solution step by step. Let’s get started!
Setup
For this challenge, I only used Registry Explorer. If you plan to use it as well, make sure to run it as an administrator.
Challenges
1. How many user created accounts are present on the system?
As explained in the room, there are multiple offline registry hives such as DEFAULT, SAM, SECURITY, and other. These hives have disk image files located in C:\Windows\System32\Config. Our goal is to know how many user accounts exist on the system. You might think, "Why not just check the Users folder in the C drive?" The problem with that approach is that the Users folder may include leftover profiles or system-created folders, which do not accurately represent valid user accounts. Instead, the SAM hive contains user account information, login information, and group information, so this is what are we looking for. The hive located under SAM\Domains\Account\Users. From there, we can identify three main accounts: THM-4N6, thm-user and thm-user2
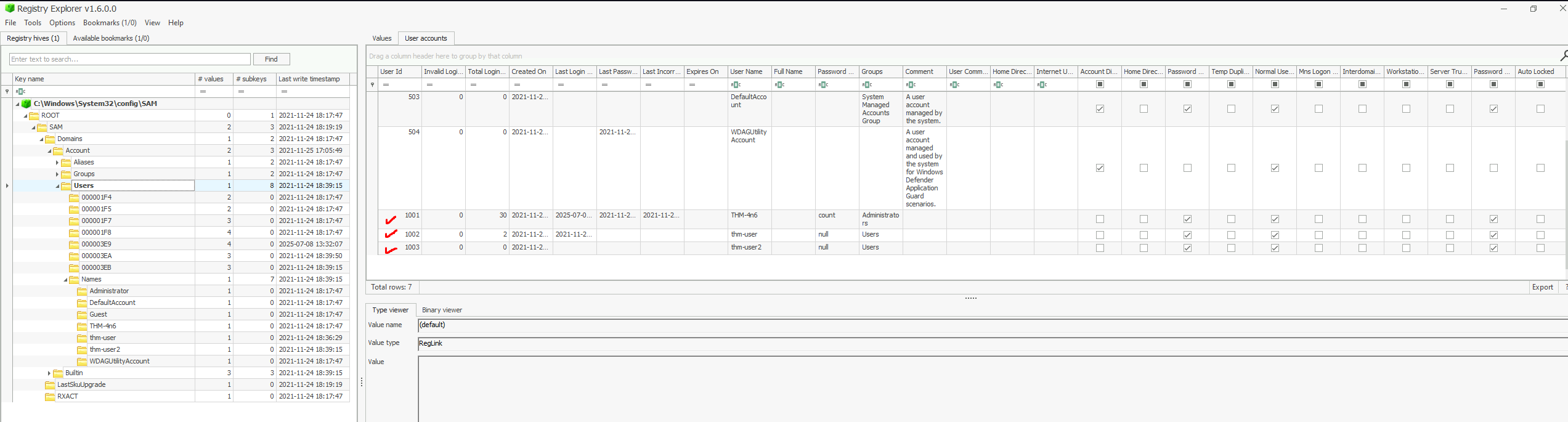
2. What is the username of the account that has never been logged in?
thm-user2 is the only user that has an empty value.
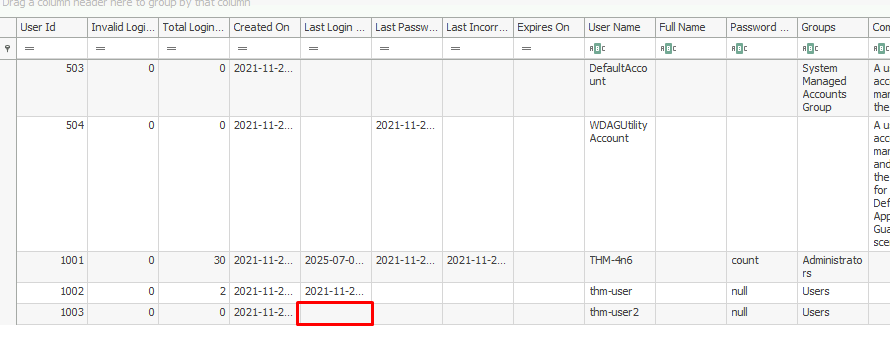
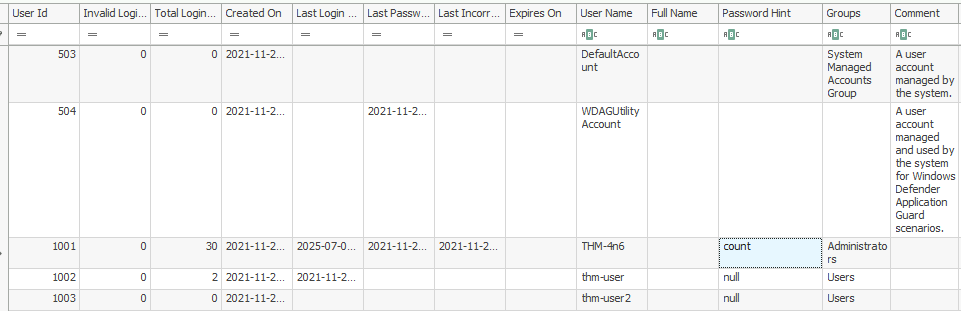
3. What's the password hint for the user THM-4n6?
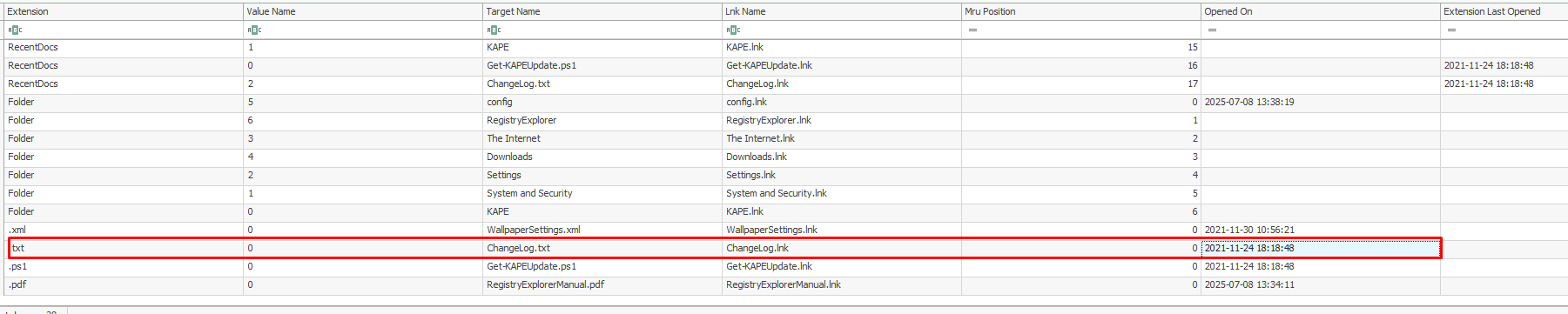
4. When was the file 'Changelog.txt' accessed?
Windows maintains a list of recently opened files for each user in the registry path: NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs. So, this is a good place to look for the information we need.
The NTUSER.DAT file is a user-specific registry hive that stores settings and information related to a user’s profile. It is located in each user's folder: C:\Users\<username>. Since it's a hidden file, you'll need to enable the "Show hidden files" option in File Explorer to see it..
Once we load the hive and navigate to the path mentioned above, we can find the file we're looking for, along with the date it was last opened:
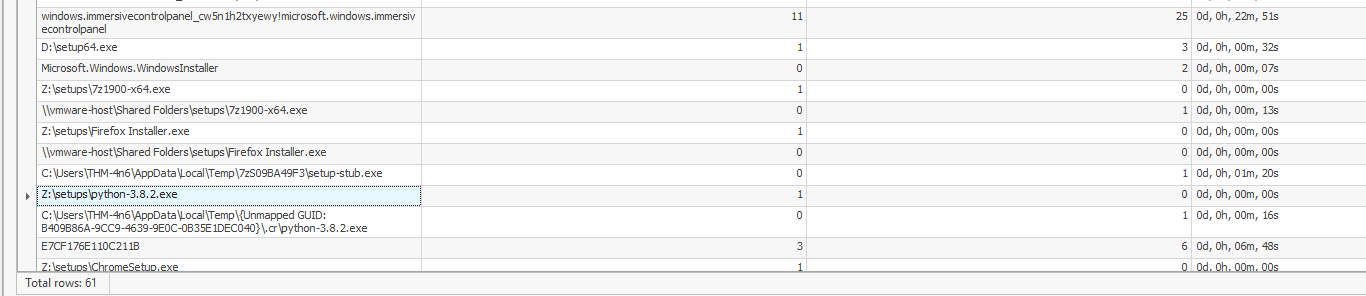
5. What is the complete path from where the python 3.8.2 installer was run?
Within NTUSER.DAT, there are registry keys that track information about programs launched by the user, including the time they were opened and how many times they were executed. This data can be found at:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count
When you navigate to this location, you’ll see entries related to various programs launched by the user, including the Python installer path:
6. When was the USB device with the friendly name 'USB' last connected?
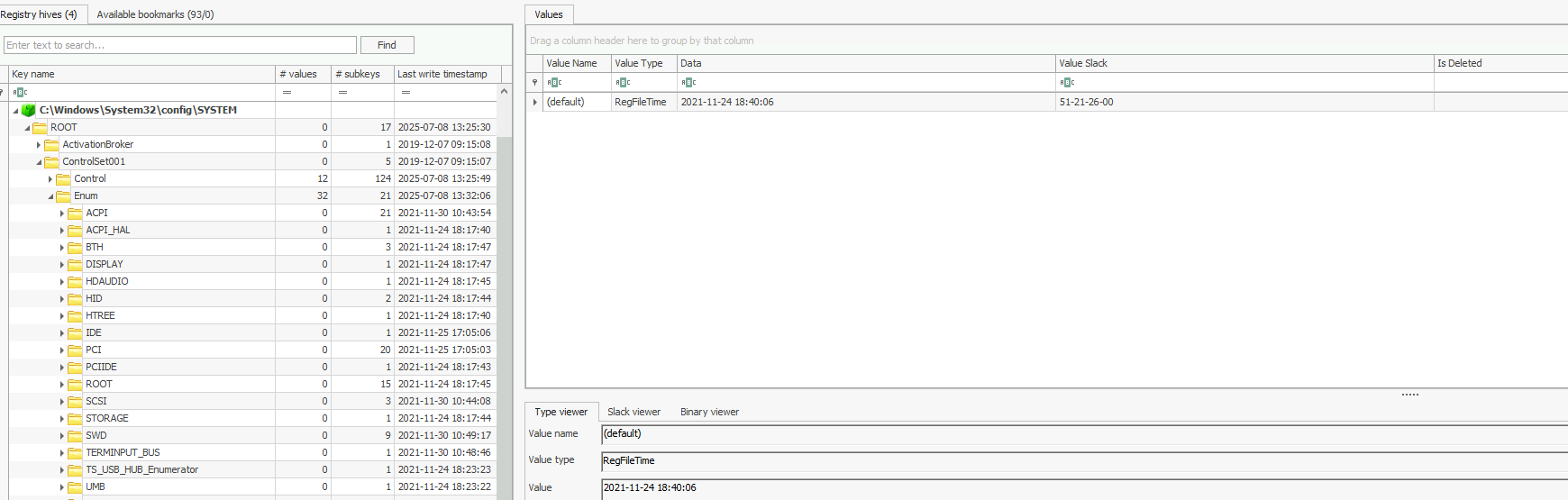
There is a registry key tracks the first time the device was connected, the last time it was connected and the last time the device was removed from the system located atSYSTEM\CurrentControlSet\Enum\USBSTOR\Ven_Prod_Version\USBSerial#\Properties\{GUID}\####. In this key, the #### sign can be replaced by the following digits to get the required information:
- 0064: First Connection time
- 0066: Last Connection time
- 0067: Last removal time
When we navigate to
SYSTEM\ControlSet001\Enum\USBSTOR\Ven_Prod_Version\USBSerial#\Properties\{GUID}
we find a subkey named 0066, which contains the answer to the question: the date and time the USB device was last connected.
In this room, I learned a lot about the Windows registry, what kind of information it stores, where to find the registry files offline, and which tools can help extract useful data. I also discovered where specific types of information are located within the registry. Overall, it was a fun and insightful experience.
Comments