HackTheBox: Web Fuzzing

Category: CTF
Posted at: Aug 30, 2024
4 Minutes Read
In this post, we'll explore the final challenge, "Skills Assessment," of the "Web Fuzzing" module from Hack The Box.
Module Section Description
To complete this Skills Assessment, you will need to apply the multitude of tools and techniques showcased throughout this module. All fuzzing can be completed using the common.txt SecLists Wordlist, found at /usr/share/seclists/Discovery/Web-Content on Pwnbox, or via the SecLists GitHub.
After completing all steps in the assessment, you will be presented with a page that contains a flag in the format of HTB{...}. What is that flag?
Let's start with directory fuzzing using feroxbuster, as it is the fastest. They mentioned that the challenge can be completed using only common.txt, so will be using it in all commands.
$ feroxbuster -u http://83.136.250.255:46777/ -w ~/snap/feroxbuster/common/common.txt 301 GET 9l 28w 325c http://83.136.250.255:46777/admin => http://83.136.250.255:46777/admin/ 200 GET 1l 2w 13c http://83.136.250.255:46777/admin/index.php
We found a directory named admin, but we don’t have access to it.
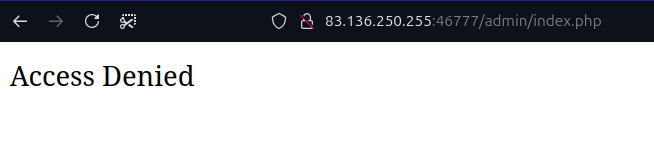
Then, I decided to perform file fuzzing using the extensions .php .html .txt
$ feroxbuster -u http://83.136.250.255:46777/admin -w ~/snap/feroxbuster/common/common.txt -x php html txt
and we got two results:
200 GET 1l 2w 13c http://83.136.250.255:46777/admin/index.php 200 GET 1l 8w 58c http://83.136.250.255:46777/admin/panel.php
We already explored index.php, so this what panel.php shows:
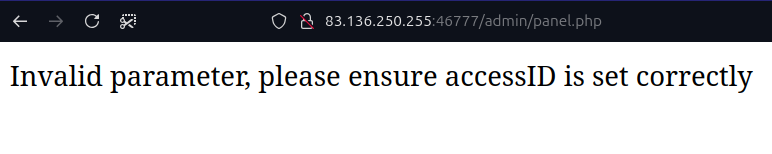
From the previous error, we can determine that the route requires a parameter named accessID. So now, let’s fuzz the parameter's value, and this time I will use ffuf:
$ ffuf -u http://83.136.250.255:46777/admin/panel.php?accessID=FUZZ -w ~/common.txt .htpasswd [Status: 200, Size: 58, Words: 8, Lines: 1, Duration: 102ms] .gitkeep [Status: 200, Size: 58, Words: 8, Lines: 1, Duration: 103ms] .subversion [Status: 200, Size: 58, Words: 8, Lines: 1, Duration: 103ms] .....
When we run this command, ffuf will print all the requests with a 200 status code by default, making it tricky to find the correct value. To solve this, we can filter out responses that are 58 bytes in size using the -fs flag. This flag will exclude every request with a response length of 58 bytes.
$ ffuf -u http://83.136.250.255:46777/admin/panel.php?accessID=FUZZ -w ~/common.txt -fs 58 getaccess [Status: 200, Size: 68, Words: 12, Lines: 1, Duration: 111ms]
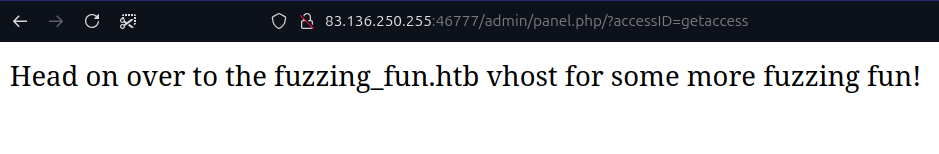
So, we’re not finished yet. It seems that there is a vhost associated with it. Let’s add fuzzing_fun.htb to the /etc/hosts file.
83.136.250.255 fuzzing_fun.htb
Note: your ip address will be different than mine
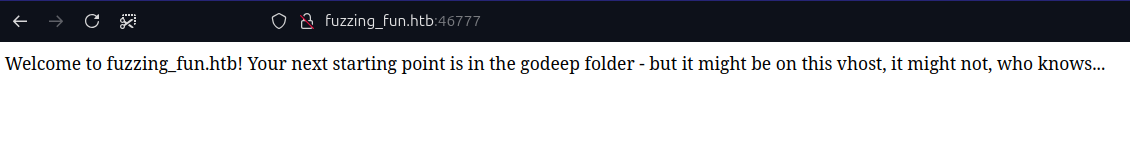
As we can see, we received a message indicating that we might be fuzzing the wrong host and that the answer is in another vhost. I couldn't find any routes in this vhost, so let’s look for other vhosts, and this time I will use gobuster.
$ gobuster vhost -u http://fuzzing_fun.htb:46777 -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt --append-domain | grep 200 Found: hidden.fuzzing_fun.htb:46777 Status: 200 [Size: 45]
I piped the output to the grep command, filtering for responses with a 200 status code, because gobuster will return a lot of responses with 403 and 400 codes.
Now, let’s add the new vhost to the /etc/hosts file:
83.136.250.255 hidden.fuzzing_fun.htb
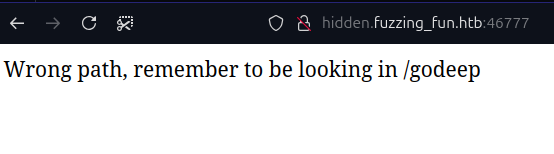
We will start fuzzing directories, again :) and don’t forget to start with /godeep:
$ feroxbuster --url http://hidden.fuzzing_fun.htb:46777/godeep/ -w ~/snap/feroxbuster/common/common.txt 301 GET 9l 28w 352c http://hidden.fuzzing_fun.htb:46777/godeep/stoneedge => http://hidden.fuzzing_fun.htb:46777/godeep/stoneedge/ 301 GET 9l 28w 360c http://hidden.fuzzing_fun.htb:46777/godeep/stoneedge/bbclone => http://hidden.fuzzing_fun.htb:46777/godeep/stoneedge/bbclone/ 301 GET 9l 28w 366c http://hidden.fuzzing_fun.htb:46777/godeep/stoneedge/bbclone/***** => http://hidden.fuzzing_fun.htb:46777/godeep/stoneedge/bbclone/typo3/
feroxbuster will automatically start fuzzing the newly found directories
and here we go!
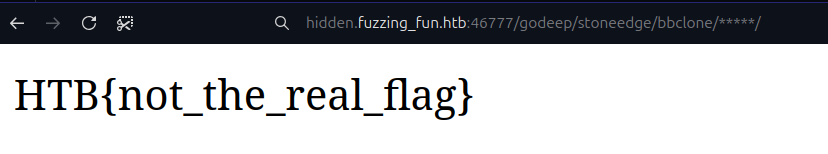
I changed the flag so you can follow the steps on your own and learn.
Good Luck!
Comments