Hack This Site - Basic

Category: CTF
Posted at: Jan 29, 2024
3 Minutes Read
HackThisSite.org is a free, safe and legal training ground for hackers to test and expand their ethical hacking skills with challenges, CTFs, and more. We will walk through the "Basic" challenges. LET'S GO!
Level 1
The password lurked in the HTML code like a secret hiding in plain sight.
<!-- the first few levels are extremely easy: password is ******** -->
Level 2
It seems that Sam forgot to upload the file, so just submit an empty password
Level 3
Upon inspecting the HTML page, you'll spot a hidden input with its value attribute set as a PHP file. This file holds the password you're after.
https://www.hackthissite.org/missions/basic/3/password.php
Level 4
Sam set up a button to email the password. All I had to do was change the hidden input value to my email address.
Level 5
Repeat the last trick, and Sam falls for it again! Sent that password flying right to my inbox.
Level 6
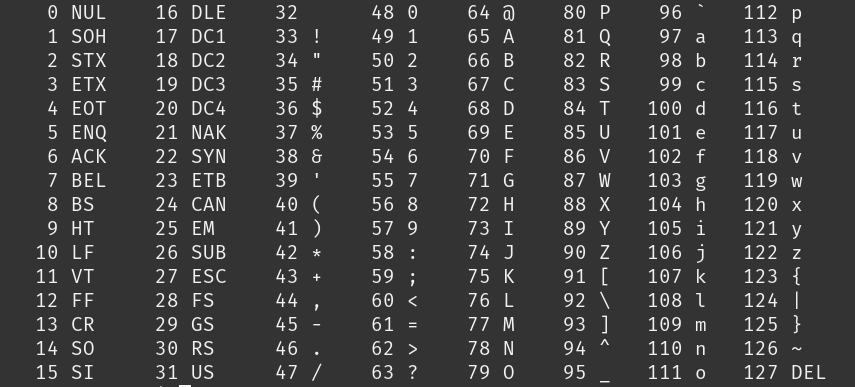
In this level, the password was encrypted using a fascinating algorithm. By utilizing BurpSuite Intruder, I deciphered the encryption method: it involves shifting characters by their position. For instance, the character '5' remains '5' because it's the first letter, while ':' becomes '7'. How? Well, peeking into the ASCII table, ':' holds a decimal value of 58. Subtracting 3 (as it's in the fourth position), we get 55, which corresponds to '7'.
Level 7
A script was connected to an input, fetching outputs from the UNIX 'cal' command. Upon testing the input for potential command execution, I successfully used '; ls' after URL encoding. This action revealed a list of files, including a PHP file with a random name. Accessing it through the browser unveiled the password.
Level 8
Sam's daughter, Stephanie, added a cool feature which prints your name and its length and generates the output in shtml file. I look for shtml payloads and I found this.
Attempting <!--#exec cmd="ls /var/www/hackthissite.org/html/missions/basic/8/" --> proved unsuccessful as it was anticipated. When I changed it to <!--#exec cmd="ls .." -->, it worked! The password was in a file with a random name, just like before.
Level 9
This level is like the last one, but here, they filter inputs from <!--. So, I tried using the previous vulnerability to find the password level's name. I used a payload: <!--#exec cmd="ls /var/www/hackthissite.org/html/missions/basic/9/" -->, and it worked like a charm!
Level 10
For this level I tried doing the previous method again but it didn’t work. I noticed A cookie held the key to this level. Changed the level10_authorized value from no to yes, and the password was mine. Who needs a golden ticket when you have cookies?